Ensuring data security in MLM: A robust defense framework for your MLM business

Introduction
Businesses are built on trust and satisfaction of customers and stakeholders. Inculcating this into every aspect of business is what will drive brands toward the larger goal of brand satisfaction. Taking care of each minor and major aspects related to customers including data privacy and security, payment security, product quality and delivery, ethical concerns, customer service, are crucial for businesses to maintain a positive brand image and foster customer loyalty.
Today, businesses are increasingly becoming data-centric, with individual business processes evolving successfully with the power of data. Factoring as an important aspect of risk management, data security is key to ensuring brand reputation and customer trust.
Data security in the digital age
In the era of digital transformation and cloud migration, data threats have only multiplied. Cloud applications and cloud infrastructure have given every individual in the business freedom to access data from anywhere, facing unexpected compromises on data security. Hence businesses today need an end-to-end solution that encompasses data security either on premises or in the cloud.
Businesses must have a complete blueprint of where their data is, who is authorized to access it, and what should be encrypted. This would save them from incurring huge financial losses and legal complications associated with data security.
Data privacy vs data security
Two different yet closely related concepts that revolve around the same entity, data, privacy and security, are equally important for businesses to consider.


Data privacy
Data privacy governs the management of data—how it is collected, used, shared, and stored while maintaining legal and regulatory boundaries. Privacy policies and regulations such as GDPR, CCPA, HIPAA, DORA, SOX, etc ensure that organizations obtain proper consent for data use from individuals. These policies may vary according to regions and countries.
During a time when identity and personal details are at stake, these regulatory bodies work towards ensuring data privacy for individuals and organizations alike.
Data security
Data security involves processes and methods adopted to safeguard data from unauthorized access, breaches, loss, or damage. Encryption, access controls, firewalls, intrusion detection systems, and regular security audits are employed to ensure security of the most crucial organizational asset, data.
Importance of data security in MLM
The data landscape in multi-level marketing is wide and complex, involving intricate details of distributors and customers. This includes personal details such as names, addresses, contact details, and sensitive financial data. The network is spread across multiple regions and countries, highlighting the need for a universal alignment of compliance and regulatory policies.
Within this complex business framework, data plays a pivotal role encompassing transaction histories, purchase patterns, commissions, sales performance, market trends, and other key organizational information. In MLM, data lays the foundation for compensation structures, sales and marketing strategies, and customer relationship management.
This volume and complexity of data calls for security and privacy measures to protect and safeguard data against unauthorized access and legal ramifications. Moreover, responsible handling of this extensive dataset is important for maintaining trust among the distributors and customers, ensuring regulatory compliance, and securing a competitive edge in the MLM industry.
A data-driven business ecosystem as MLM records, analyzes, and leverages customer and distributor interaction to propel the business forward, making data security and maintaining privacy paramount.
Why data security matters for MLM companies
Given the importance of data in multi-level marketing, what really matters in securing data is the trust and confidence that accompanies it. Multi-level marketing despite being a genuine marketing model with sizable potential, is often eyed with suspicion mainly due to unethical business practices.
However, customer-centric companies in the industry have amassed considerable appreciation with a striking level of customer-distributor satisfaction and trust. Maintaining high data security standards helps foster customer trust and brand reputation. It also safeguards businesses from incurring huge financial losses attributed to data breaches and non-compliance. Data breaches not only affect the company’s revenue but also act as a detrimental factor to brand reputation.
There is an impending need for customers and distributors to feel secure that their information is always protected. Mitigating the risk of unauthorized access to the MLM database can reduce data threats to an extent. Demonstrating ethical and transparent data security practices can also prove a competitive advantage for MLM businesses with distributors and customers choosing brands that prioritize data security.
Understanding data security in MLM
Data security in MLM is built on three core principles—confidentiality, integrity, and availability. Every business in the network marketing industry must work hard on implementing these tenets to ensure extended customer satisfaction, distributor loyalty, and unwavering brand reputation.
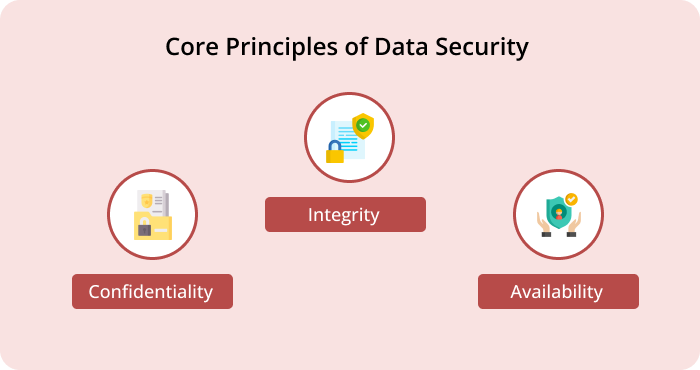
Confidentiality
Aimed at preventing unauthorized access and disclosure of information, confidentiality ensures data is accessible only to those who need it, limiting access to safeguard organizational data.
Confidentiality of organizational data is best implemented through access management and controls. Multi-factor Authentication (MFA) and Single Sign-On (SSO) are the common methods employed to manage access controls. Encrypting data and using encrypted connections can also help maintain the confidentiality of data.
Integrity
This principle focuses mainly on unintended or unauthorized manipulation of data. It ensures accuracy and reliability throughout the data lifecycle.
It enhances the trustworthiness of data through secure password management, regular data audits, checksums and hashing, digital signatures, and database constraints.
Availability
Availability in data security emphasizes real-time accessibility of data for authorized users when needed. It focuses on reducing downtime and disruptions ensuring accessibility, reliability, and responsiveness to users.
MLM businesses can ensure uninterrupted availability of data to its users by opting for methods such as DDoS, robust monitoring systems, and an updated incident response plan in place.
Legal framework governing data security in MLM
Multi-level marketing is a business that always falls under the strict scrutiny of legal and regulatory authorities. For MLM businesses to ensure smoother operations, a solid legal and compliance framework is important.
Apart from global regulatory bodies reinforcing data privacy, industry regulatory authorities like DSA and DSSRC constantly monitor businesses and issues strict guidelines to ensure that the businesses and their stakeholders always maintain ethical standards and compliant business practices. Mandates related to earning claims and compliance are regulated by federal agencies like FTC, SEC, and other self-regulatory organizations.
Data security: A competitive advantage
Having a strong data security framework helps MLM organizations gain an edge over the competition by fostering trust among customers. It gives customers and distributors reassurance that their data is in safe hands thereby improving brand engagement and trust which eventually contributes to long-term brand loyalty and reputation.
Adopting robust data security measures help shield the brand against threats and attacks. Companies can also position this as their value proposition to differentiate their position in the competitive market.
Additionally, aligning with the data protection laws and regulations and demonstrating a commitment to ethical business practices not only helps brands avoid legal penalizations and hefty fines but also elevates brand image in the eyes of their customers.
Common threats to data security in MLM
Data threats of varying sizes and intensities hit MLM businesses creating an irrevocable loss on finances, brand reputation, and customers. While companies adopt various measures to curb attacks, many other internal and external factors impact its efficiency.
Most common threats detrimental to MLM businesses are:
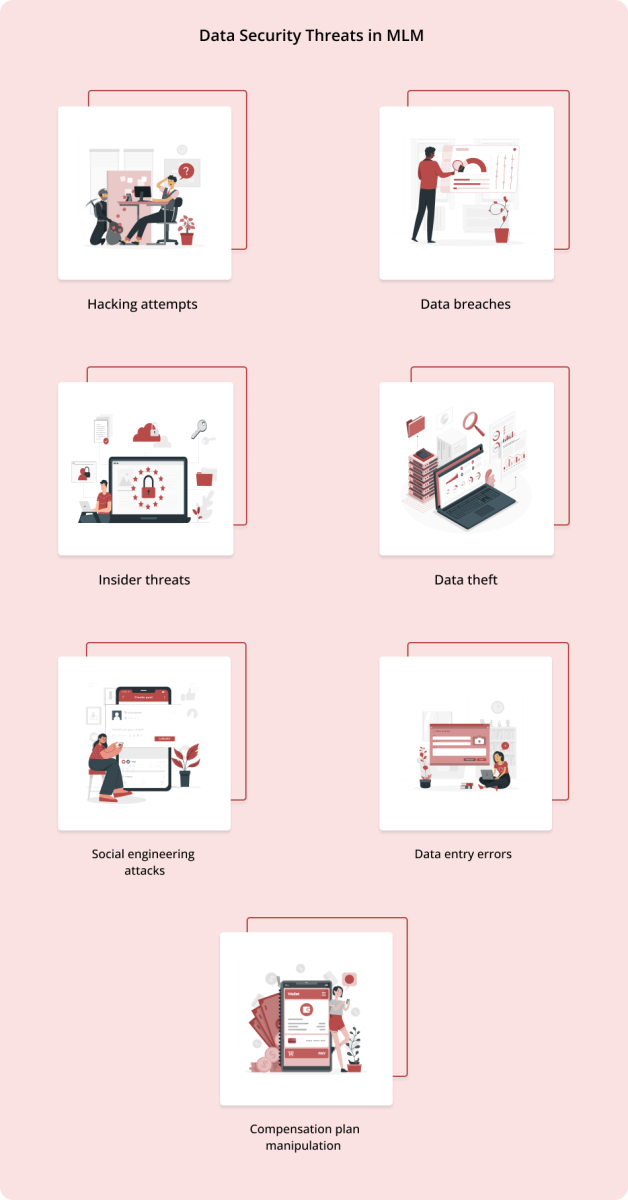
Data breaches: Unauthorized access to sensitive information can result in the exposure of personal or confidential data of the business and its stakeholders.
Hacking attempts: Aimed at exploiting vulnerabilities in the security systems, attack methods like phishing, ransomware, malware, and SQL injections are employed by hackers to gain unauthorized access to systems, networks, or databases.
Social engineering attacks: Attackers employ manipulative techniques to deceive individuals into disclosing sensitive information through phishing emails, pretexting, baiting, etc. This method exploits psychological aspects of an individual rather than technical vulnerabilities.
Insider threats: Individuals inside the organization may intentionally or unintentionally compromise data due to various reasons. Insider threats mostly arise out of negligence, lack of awareness, or malicious intent.
Data theft: Personal, financial, or confidential data of customers or distributors are attractive targets for hackers. Once stolen, they use it to commit identity theft or other illicit activities.
Compensation plan manipulation: Individuals may exploit the system to alter compensation plans for their personal benefit. This includes misinterpreting performance metrics, sales volume, commission percentages, ranks, etc to increase their compensation.
Data entry errors: Manual systems can create grave errors while entering data related to commission calculations, compliance agreements, customer and distributor information, and other related processes.
Unique data security challenges faced by MLM businesses
In addition to grappling common business challenges, MLM companies also encounter a distinctive set of internal and external challenges. These challenges hold back businesses and their salesforce from achieving their full potential.
Distributed network vulnerabilities
MLM companies have vast distributor networks, with distributors accessing the system from almost anywhere. This creates a decentralized environment that can be challenging to secure uniformly.
Complex compensation structures
MLM businesses operate on complex compensation plans making it difficult to detect manipulations and flaws easily. Ensuring accurate and secure processing of financial transactions is crucial to prevent manipulation and revenue drain.
Non-compliance and regulatory penalties
An industry under constant vigilance, businesses operating in the MLM industry often find it hard to align with the compliance policies of various regions that require constant adaptation. Violating data security regulations can incur potential legal consequences associated with financial penalties.
Data loss due to hardware failure
Hardware failures such as hard drive crashes, RAID array issues, or malfunctioning of storage devices can all contribute to unexpected data loss. A robust backup strategy coupled with monitoring tools and data recovery plans can help businesses recover data in the event of failure.
Inadequate access controls
MLM companies have distributors walking in and out of business frequently. Such a dynamic environment complicates access control and user management letting companies walk into the danger of granting unauthorized access to sensitive data. Access control systems must be capable of revoking and granting access promptly.
Lack of encryption
Unencrypted data is at the risk of falling into the wrong hands. Lack of encryption aids attackers in accessing and manipulating data putting the confidentiality and integrity of data at stake. Transmitting data without encryption exposes both individuals and organizations to a multitude of legal, regulatory, or financial consequences.
Keeping pace with the rapidly evolving threat and security landscape and adopting new methods to counter attacks can be demanding. Addressing these challenges requires a holistic approach combining technological solutions and proactive cybersecurity strategies.
Build stronger business credibility by integrating industry-leading security features embedded in an MLM platform.
Secure your business nowRole of MLM software: Key functions governing data security in MLM
Technology is cutting long processes short for businesses to operate seamlessly in the global marketplace. However, operating in a dynamic and complex business landscape, MLM companies require innovative and tailored technology solutions that are agile, scalable, and responsive to the unique challenges of the industry.
In the field of data security, the role of MLM software is predestined for the fact that tailored MLM solutions analyze data, identify unique needs and gaps in the business framework, and propose solutions to fortify data security measures.
MLM software safeguards data against potential threats and vulnerabilities through a strong strategic framework. The resilient architecture of MLM software ensures the security and confidentiality of customer, distributor, and organizational data.
Role-based access controls
MLM software implements strict access controls on data accessibility minimizing the risk of unauthorized access. Admins and distributors are given specific privileges limiting their access to specific data and functionalities as demanded by their role within the organization.
Data encryption
Employing various encryption algorithms like AES (Advanced Encryption Standard), RSA and methods like SSL/TLS help encrypt data during transmission and storage. MLM software enforces user authentication through authentication mechanisms like username and password, Single Sign-On (SSO) and Multi-factor Authentication (MFA).
Secure payments
MLM software supports a wide array of payment methods and gateway integrations that comply with Payment Card Industry Data Security Standard (PCI DSS) to ensure the security of financial information during transactions.
Data backup and recovery
The data backup and recovery feature in MLM software ensures that data is regularly monitored and backed up. This guarantees the safety of data during unexpected system failures or security breaches.
Compliance monitoring
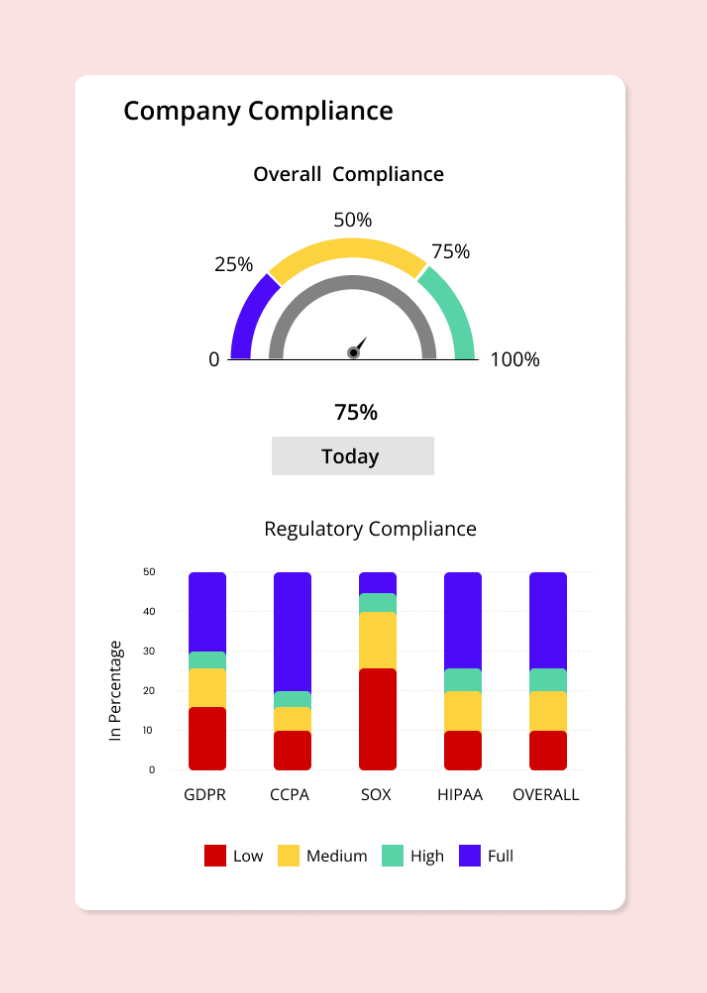
MLM platforms ensure that businesses operating in the network marketing industry are in strict adherence to global compliance standards such as DORA, GDPR, CCPA, SOX, HIPAA, etc. Automated compliance monitoring help businesses stay updated on the changing compliance policies across regions.
Intrusion detection and prevention
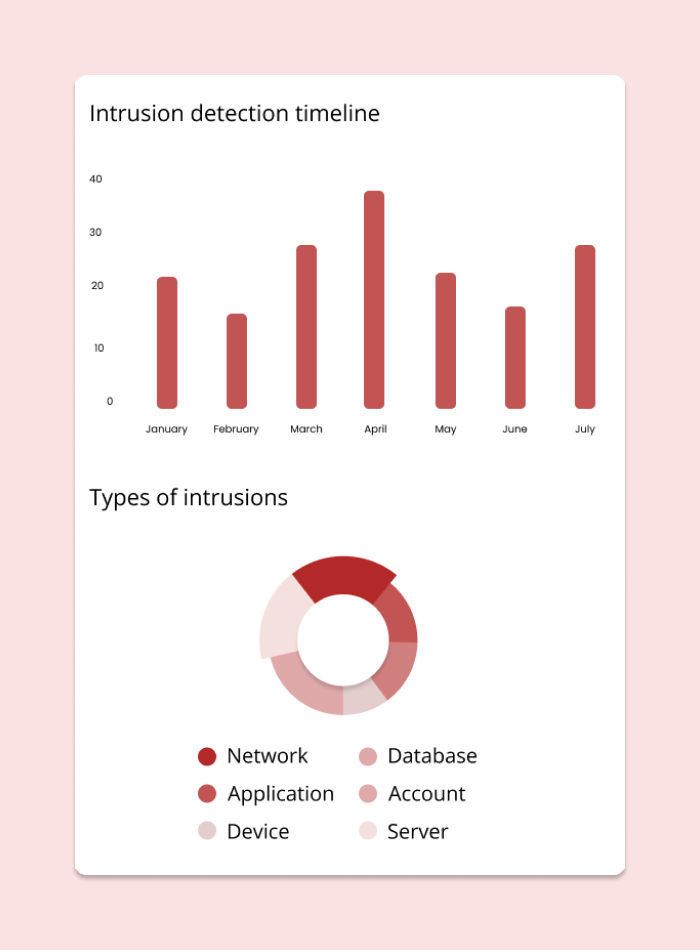
Intrusion detection and prevention (IDP) is a mainstream feature for ensuring network security. It monitors systems for malicious or suspicious activities and adopts proactive measures to block potential threats.
Audit trails and loggings
Detailed audit logs track user activities to help detect any unauthorized or suspicious activity in the system and maintain the integrity and security of data.
Maintaining high standards of privacy and compliance is important for protecting the data of customers and distributors. While this serves as a cornerstone for building a strong brand reputation, it also helps businesses save data from hidden risks.
While adopting technology is inevitable, fostering a culture of continuous adaptation is crucial, ensuring that the technology solutions evolve in tandem with the ever-evolving MLM landscape.
Customer success stories: How leading MLM companies are navigating success
Best practices for data security in MLM
Implementing robust security measures resonates with a brand’s commitment to ethical and responsible business practices. In addition to safeguarding sensitive information, preventing unauthorized access and protecting user privacy, maintaining data security best practices can help MLM businesses align with compliance and regulatory standards while operating in the global arena. It also builds trust among stakeholders and customers safeguarding the reputation of the organization.
Regular training and awareness programs
The best and most effective way to implement data security is to keep the salesforce and stakeholders informed on the importance of maintaining data security within the organization through regular training and awareness programs. This can not only mitigate risks but also cut short data security threats that arise out of negligence.
Robust password management system
MLM organizations must enforce strong password requirements to gain access to the system. Implementing unique and complex password requirements and regular password updates can considerably reduce the risk of unauthorized access. Methods like Multi-Factor Authentication and password encryption can optimize access management measures.
Data classification
Categorizing data based on sensitivity and importance helps MLM companies adopt appropriate measures to secure data. It helps manage risks by identifying and prioritizing data based on potential risks, allowing organizations to allocate resources effectively. Data classification is also effective in raising user awareness about the importance of handling different types of data and understanding the consequences of mishandling sensitive information.
Data encryption
Implementing standard encryption protocols is a robust defense mechanism in an MLM organization’s overall data protection strategy. Practicing data encryption even for less important data can help maintain the confidentiality and integrity of organizational data. Converting data into a secure format can help guard data against cyber attacks making it difficult for attackers to access and interpret stolen data.
Regular updation of access controls
MLM organizations must, from time-to-time, monitor and update access controls to ensure that sensitive information is accessible only to authorized personnel. Maintaining a dynamic and responsive access control system is integral to creating a resilient security posture. The access rights should be promptly revoked or updated based on the user’s current roles and responsibilities.
Regular security audits
Routine data security audits help detect vulnerabilities, strengthen data defense framework, and ensure compliance with industry and organizational policies. Performing security audits also improves data governance practices and performance. Data security audits are also an effective way of benchmarking an organization’s security management strategies and operations. Feedback and insights derived from audits can be used to update data security policies, optimize training programs, or improve data security strategies.
Incident response plan
Attackers often outsmart and bypass companies’ defense mechanisms to gain control over organizational data. In the event of such incidents, a robust incident response plan can come to the rescue by addressing and mitigating potential breaches. Having a dedicated incident response plan can detect anomalies, notify them promptly, and isolate affected systems or networks to prevent further damage. In addition to addressing attacks, an incident response plan can analyze the root cause of the incident and implement necessary steps to prevent future occurrences. However, in an evolving threat landscape, the company’s incident response plan should be put to regular testing and upgrades.
Vendor due diligence
MLM business involves distributors and other third-party vendors accessing the MLM system from various places, public or private, secure or insecure. MLM organizations must make it a practice to strictly adhere to robust security standards while communicating with third-party vendors through the system. The data protection policies, procedures, and protocols of vendors should be assessed from time to time to ensure that it aligns with organizational standards and complies with relevant industry regulations.
Data backup and recovery
Backing up even the smallest data elements counts toward the overall health of an organization’s data ecosystem. Employing an automated data backup procedure safeguards data against hardware failure, cyber attacks, or accidental deletion. MLM companies should opt for reliable modern day data backup solutions like cloud storage, external hard drives, network attached storage or hybrid solutions taking into consideration factors like data volume, accessibility, and recovery speed.
Secure communication channels
Secure communication fosters trust among distributors and customers by protecting information from unauthorized access and manipulation during transmission. By implementing strong security protocols like HTTPS or TLS/SSL for web traffic and VPN for private networks, organizations can contribute to security by encrypting data and connections during communication.
Regular software updates
Outdated software is always an easy target for attackers. Keeping all software and systems up to date makes it easier to detect and address vulnerabilities that could otherwise make data a potential point for attackers. Software updates often improve security systems providing better protection against malware, viruses, and other cyber attacks. It ensures interoperability allowing new systems to work seamlessly together. Updating software on compliance and regulatory standards also helps businesses align with industry regulations.
Data compliance
An obligatory aspect of data security, maintaining legal and regulatory standards during collection, storage, processing, and sharing of data is important for businesses to protect user privacy, maintain trust, and avoid legal ramifications. Aligning organizational data policies to global data privacy standards such as GDPR, CCPA, HIPAA, SOX, DORA is inevitable for businesses to operate in the global markets. Establish a flexible and well-informed data policy wherein user consent is obtained before collecting and processing data and facilitate their right to access, edit, or delete their personal data.
Business continuity planning
Business continuity planning includes identifying potential risks, developing strategies to mitigate these risks, and ensuring the availability of resources to maintain uninterrupted business processes during and after disruptions. Having a business continuity plan ensures availability of data and uninterrupted operation in the event of an attack. Employing redundancy and failover mechanisms can ensure business continuity even if any of the software or hardware component fails. Developing clear communication plans and training internal and external stakeholders can assist businesses during emergencies.
Data security policies
All MLM organizations must have robust security policies, primarily to safeguard sensitive information and to align with compliance requirements. Organizations must make it a practice to update and communicate changes in policies to all stakeholders. Policies on password security, network security, and device security must be constantly monitored to alleviate the intensity and frequency of data security incidents. Data security policies must align with the preferences of customers, and they should always be kept in the loop regarding policy changes and updations.
Documentation and record keeping
Maintaining a history of security measures and incidents assists businesses in the identification of vulnerabilities and attack patterns. Proper documentation and record-keeping also give a comprehensive view of the security protocols, access controls, and user activities. This proactive approach to data security acts as an important resource for training users, devising incident response plans and adopting improved strategic measures. A well-documented security framework becomes a strategic asset to the organization facilitating prompt adaptation and resilience during threat incidents.
Common data security mistakes to avoid
Mistakes in handling data can weigh heavily on a brand’s reputation. Here are the most common data security mistakes companies must avoid in order to reinforce customer satisfaction and trust.
Neglecting regular software updates increases chances of security attacks making the software unreliable and outdated.
Weak password practices lead to unauthorized access resulting in data breaches and identity thefts.
Insufficient backup protocols put organizations at the risk of losing critical data causing operational disruption.
Ignoring compliance requirements causes MLM organizations to face legal consequences, affects financial health, eventually resulting in reputational damage and loss of business opportunities.
Neglecting data breaches compromise personally identifiable information of distributors and customers, and intellectual data of organizations.
Lack of device security can increase the risk of malware infections leading to data breaches, intellectual property theft, identity theft, and potential financial harm.
Unsecured Wi-Fi networks expose vulnerabilities allowing unauthorized access compromising the privacy and integrity of transmitted data.
Neglecting data security training leaves users unaware of the potential threats and best practices making users and organizations vulnerable to cyber threats.
Insufficient access control leads to unauthorized users gaining access to sensitive information, compromising privacy and causing potential misuse.
Ignoring regular security audits can cause a series of concerns such as increased cyber attacks, inability to identify vulnerabilities, non-compliance, and inability to maintain a robust defense mechanism.
Lack of incident response plan in the event of an attack can lead to prolonged downtime, data loss, financial, and reputational damage.
Vendor oversight leads to supply chain vulnerabilities and compromised systems, making it difficult to maintain a secure and resilient business ecosystem.
Missing data security policies leave businesses without clear guidelines for handling sensitive information, risking non-compliance with industry regulations.
Inadequate documentation creates issues regarding proper functioning of security measures, also devoiding companies an insight into past handling of threats and breaches.
Adopting ethical data practices in MLM
Ethical business practices are trust factors that bind customers and brands together. It elevates brand reputation, fosters trust and is a solid foundation for realizing consistent success in a brand’s marketing efforts. Listed below are the key steps to ensure ethical data handling within MLM companies.
Establish transparency by communicating how the collected data will be used.
Always obtain user consent before using their personal information.
Make it a point to collect only the relevant details.
Adopt prompt security measures to safeguard customer and distributor data.
Maintain data accuracy by keeping data up to date.
Conduct regular training sessions for employees and distributors on ethical data practices.
Maintain strict compliance standards.
Embrace ethical and transparent marketing practices.
Enforce data protection policies that align with legal requirements.
Appoint Data Protection Officers (DPOs) to provide guidance for organizations and its stakeholders on various aspects of data management and security.
Future of data security in MLM
In the rapidly evolving threat landscape, the need for organizations to stay vigilant has only multiplied. Maintaining strong data security standards has also become a distinguishing factor in the competitive marketplace.
Technology
Technological advancement shapes and sizes data security every day impacting the way organizations prioritize and manage their security standards.
The growing trend in data management is governed by transformative AI, cloud-based solutions, machine learning for multi level marketing, and blockchain. These emerging technologies are leading the way to a more sustainable future by enhancing security measures. AI-driven threat detection, blockchain for secure and decentralized transactions, implementation of zero-trust frameworks, are all redefining organizational strategies in battling cyber threats.
Replacing the negatives of traditional centralized data environment, a decentralized data environment that runs on blockchain ensures improved data privacy and security. Additionally, users will have full control of their data ensuring that their data remains defiant and secure and can only be accessed based on the user consent. This way, responsibility is evenly shouldered by users and organizations.
Regulations
With every passing day comes new restrictions and privacy regulations. The potential impact of establishing new security and compliance standards on MLM businesses will need a system that can align with the changing regulatory landscape. With the possibility of stricter laws and enforcement by regulatory authorities, MLM businesses must take stringent measures in training and adapting their salesforce to the changing policies to avoid financial and reputational damage and foster brand trust.
Advanced authentication methods such as biometric scans and hardware tokens are more secure than password-based encryptions. Biometric authentication methods such as facial recognition, eye scanners, fingerprint scanners, and voice recognition prevent identity theft ensuring users a high-level security to their personal data.
MLM companies can reinforce customer trust through third-party security audits. As opposed to first- and second-party audits, third-party security audits are more convincing for customers since they involve impartial audits of a company’s security standards.
Global data governance
Global data governance refers to the cross-border regulation and management of data policies, standards, and practices. It ensures that data is handled in compliance with relevant regulations on a global scale. In the MLM context, companies often operate in multiple countries with different data policies and regulations. Implementing a robust data governance framework with relevant policies and procedures elevates data security safeguarding customer and distributor data which would otherwise cause serious legal repercussions. By demonstrating a commitment to ethical and responsible data practices, MLM brands can build trust among customers and distributors, transforming themselves into a global brand.
In addition to gaining operational efficiency, global data governance can help companies derive cross-border insights into business performance, market trends, and customer behavior.
Discover how high-end, encrypted MLM software can protect your business from potential data breaches and their far-reaching consequences.
Request demoConclusion
Leaping forward into the future, MLM companies must rethink their data security investments. Not only does it offer a cost-effective solution to data management, but also shields the company against future attacks and data losses. Customer and distributor trust is based on the level of security and privacy a company provides. It moreover underlines the value and commitment of a brand to preserve the right to privacy and information of its users. In such a data-driven environment, focusing on data security investments will help companies sustainably lead their race amidst soaring competition.
- Introduction
- Data security in the digital age
- Data privacy vs data security
- Importance
- Why data security matters
- Understanding data security
- Legal data security framework in MLM
- Competitive advantage
- Common threats
- Challenges
- Role of MLM software in data security
- Best practices
- Common mistakes to avoid
- Ethical data practices
- Future
- Conclusion
Epixel MLM Software anchored 100+ network marketing companies to success through their business process automation in more than 88 countries. Let Epixel MLM Platform revolutionize your MLM business with 100+ proven features intelligently tuned for small, medium, and large enterprises.